The COVID-19 pandemic is creating an urgent need for technical solutions to assist in the critical process of digital contact tracing. In a recent blog, Christopher Luise and guest co-author Daniel Schwartz discussed contact tracing at a high level as well as the privacy and legal ramifications of proposed digital contact tracing solutions.
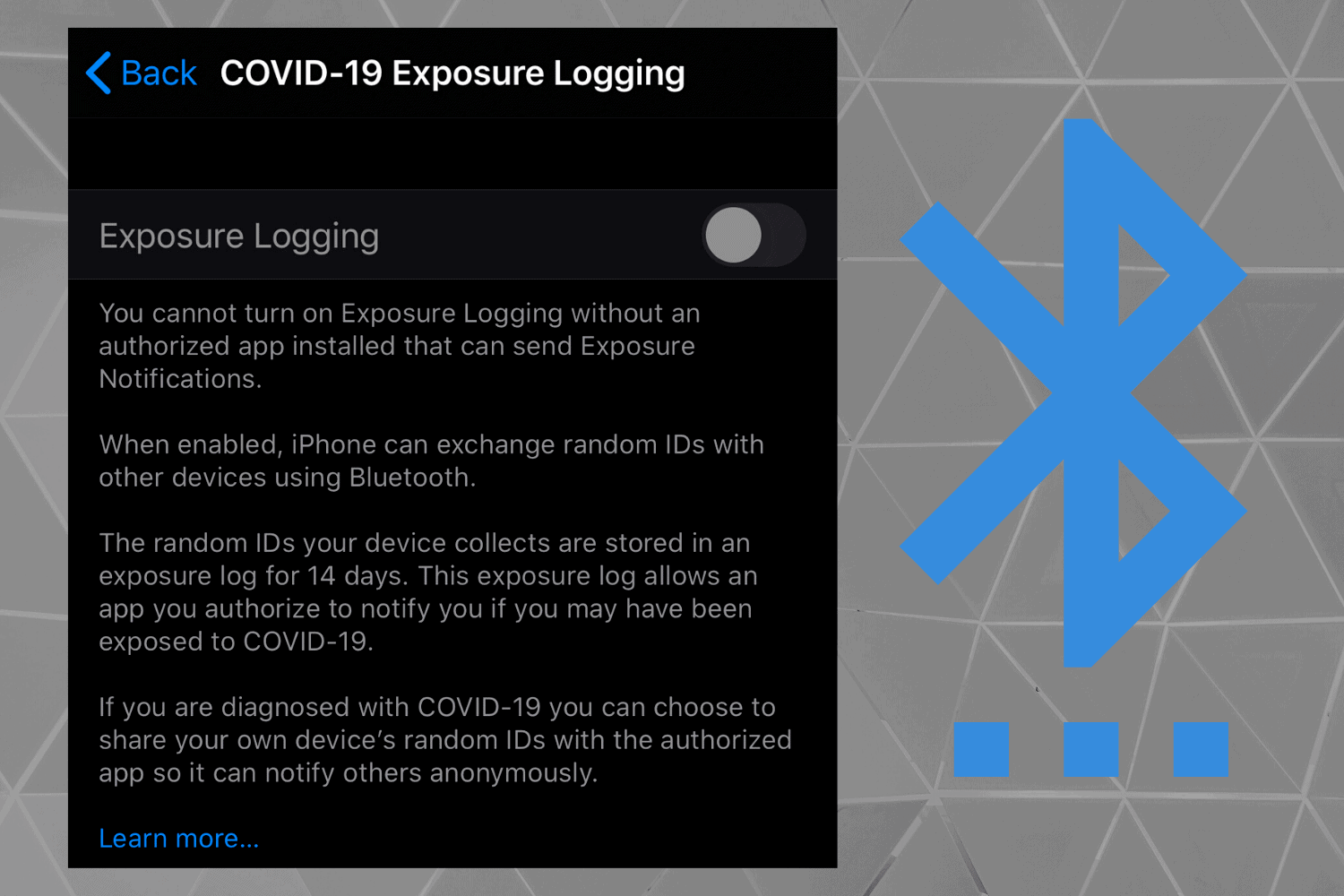
Apple released iOS 13.5 to the general public today, including a new feature called COVID-19 Exposure Logging, based on the exposure notification API framework Apple developed with Google. Android users will receive Google’s update automatically via Google Play Services. In this blog, I’m going to take a deeper look at how these exposure notification solutions work from a technical perspective and the potential security considerations.
What is BLE?
The technology leveraged in mobile device-based contact tracing system is Bluetooth Low Energy (BLE). BLE has been around for the last decade, since Bluetooth 4.0 specifications were first adopted. BLE has been built into all smartphones for years.
When we think about Bluetooth technologies, we tend to think of consumer-focused items such as headsets, speakers and wearable devices like the Apple Watch. These devices all use standard Bluetooth technology to handle the large data streams required to connect these peripherals to our mobile devices. For example, think of how much data transmits when you’re listening to streaming audio via your Bluetooth headset.
BLE is for a different type of application – apps that don’t need as much bandwidth as Bluetooth but require quick communication. For example, while the data-heavy Apple Watch uses the full Bluetooth technology, other types of wearable technologies such as Fitbit devices use BLE instead. You will also find BLE used widely in Internet of Things (IoT) devices. Healthcare organizations often use BLE for blood pressure, temperature and glucose monitoring devices.
Why Use BLE?
The primary reason for using BLE over Bluetooth is the significant difference in power requirements. To support the high level of data transmitted, Bluetooth uses a lot of power and drains battery life very quickly. The nature of BLE communications is short “burst” type transmissions not requiring a lot of power. As a result, it can support a much longer battery life.
One of the more popular (and scary) uses of BLE is an advertising technique called proximity marketing. In one use case, a retailer can install beacons in their stores. When users gets close to a specific area of the store, the beacon sees that a mobile device is nearby. Phones advertise their location (unless the user manually disables these services on their phone) and then a targeted advertisement sends to that user’s mobile device. Have you experienced this at an Apple Store yet? That’s proximity marketing in action, talking to an iPhone.
How Will Digital Contact Tracing Work?
Now that I’ve covered the background on BLE, let’s talk about how COVID exposure notification is projected to work. I use the word “projected” intentionally. It is important to note that Google and Apple’s joint announcement pertains only to the API (Application Programming Interface, otherwise known as a developer framework) they are making available on their mobile device platforms. To be clear – there has been some confusion on this point – Google and Apple are not actually creating digital contact tracing applications, at least not yet (there are discussions that Apple may do this in the summer). They’ve created the API and the framework that will allow application developers to create contact tracing applications that leverage the BLE functions of Android and iOS devices.
Here’s what the Apple/Google announcement means from a security perspective: not only do we need to be aware of the security concerns associated with the API framework, we will also need to do a security review of any and all contact tracing applications separately.
How the system is projected to work:
- Bill and Jane both install and opt-in to the contact tracing application.
- Bill and Jane meet for lunch. As a result, their phones are within close proximity for a period of time, and the phones communicate to each other using BLE.
- Later, Bill positively diagnoses as having COVID-19. He submits an update on his contact tracing application.
- Jane’s contact tracing application periodically checks into the public health tracking system. The app notifies Jane that she recently came across someone who was COVID-19 positive. The notification also gives Jane information about the next steps she should take.
Digital Contact Tracing/Exposure Notification Security and Privacy Concerns
The application of mobile device technologies for use in this pandemic represents a major leap, but has led to valid concerns regarding security and privacy. From a security perspective, my biggest concern about the use of BLE is the potential for identity tracking – that is, being able to determine the identity of the user from the BLE communications sequence. As we transition to talking about how BLE will work with digital contact tracing and exposure notification, this is one of the biggest potential issues that needs to be addressed.
The standard developed by Apple and Google works to address these concerns in several ways:
 Opt-In Model
Opt-In Model
The exposure notification feature will be disabled by default. Users will have to make an “explicit choice” to enable the functionality and according to Apple, exposure logging cannot be turned on until an “authorized app is installed that can send Exposure Notifications”. Once enabled, the user retains the ability to turn it off at any time.
Bluetooth Allows for Greater Privacy than GPS
The choice of Bluetooth over GPS for the contact tracing and exposure notification framework is significant. This greatly reduces the potential for these applications for tracking individuals. The use of BLE allows the applications to understand who the users are in proximity (and for how long) without exposing sensitive location information (which GPS could possibly provide).
Device Identifying Information is Random
The standard addresses privacy concerns by randomizing device identifying information. This means that if you receive a notification, it is not easily possible to backwards trace the identity of the person that infectious exposure was with.
Apple and Google have created a framework to address how to keep user identities private to address the concerns about users not being able to be identified. Specifically, the standard calls for the development of the following:
-
- Temporary Exposure Keys – Generated randomly, these keys change daily. Stored in an exposure log on your device for 14 days, the random IDs can be deleted by the user.
- Encrypted Bluetooth Data – Encrypting the Bluetooth metadata helps protect user anonymity.
- Rolling Proximity Identifier – Broadcasts by the mobile device as the “advertisement” to initiate BLE connection between devices. This identifier sets to change every 15 minutes, which prevents user tracking wirelessly.
Open Questions
As I mentioned earlier, Apple and Google are not developing the actual digital contact tracing applications for COVID-19 tracking. We don’t have the specific applications to review and comment on yet. However, it’s imperative that we get answers to the following questions.
Question #1 – Who stores the data and how do they use it?
This is the most significant question of all. If we are trusting our most sensitive personal data to benefit the greater good, we must know the answers to:
-
- How will the data be used?
- How long will the data be retained?
- What safeguards/protections will be in place to prevent the data from being monetized or used for other non-intended purposes?
- Who will have access to this data? For how long?
- Can this data be legally discoverable?
There are huge trust issues here. History teaches us that as we give up more of our data, its use is not always for the intended purposes. Widespread adoption of contact tracing applications will not take hold if these data privacy questions are not adequately addressed.
Question #2 – How do we prevent false positives?
What types of verification will prevent someone from claiming that they are COVID-19 positive when they’re not? Without safeguards built in, malicious users could flood the system with false positives. This could create panic and otherwise diminish the effectiveness of the systems (somewhat like a denial of service attack).
As applications develop, we will need to take a deeper dive into the applications and the system. A small number of widely adopted applications would be ideal. More information will likely lead to more questions, but as always, we’ll provide guidance as we learn more.
