
Willie Sutton was a notorious bank robber and serial prison escape artist (escaping three separate times) that stole approximately $2,000,000 between the 1920’s and 1940’s. Willie is most noted though for a famous quote (which he later denied saying). When asked why he robbed banks, he stated “because that’s where the money is.”
Fast forward to 2018 and we in the industry are seeing a huge spike in phishing attacks against Office 365 users. Why O365? Simple, it’s where the users are now. In 2017, Microsoft reported that their monthly active user count surpassed 100 million users. In the words of Maverick (from Top Gun), “that’s what I call a target rich environment.”
In these attacks, end users are getting emails that appear to come from legitimate sources – such as internal IT administrators, other users or colleagues – that tell them there is a problem with their email account and they need to go to a specific link and enter their Office 365 credentials (see image below). Once the user has clicked the link and given that information, the attacker “owns” their mailbox. The attacker not only has the ability to see, read and forward anything that is stored in their Outlook, but the attacker can also then use this mailbox to send out more malicious requests.
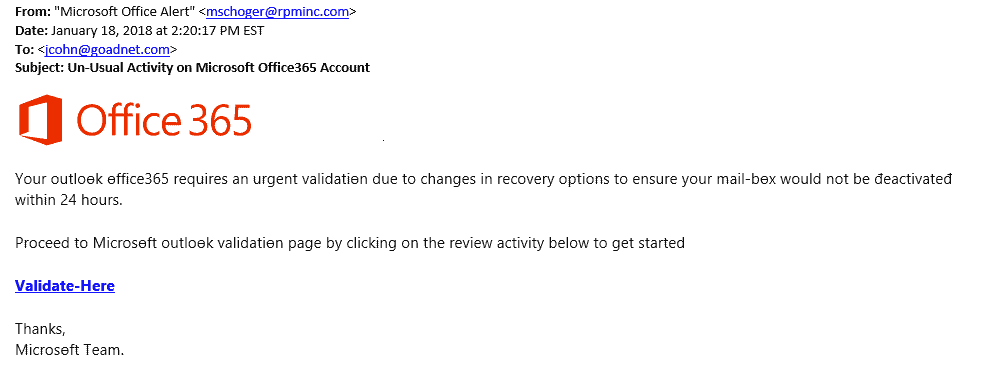
This unauthorized access to a person’s mailbox is problematic enough, but with Office 365 the issue can be much, much worse. As more organizations move their file storage and other critical systems to the cloud, this one set of credentials could be used to access any and all of that information. That creates a compliance and privacy nightmare for all organizations. Protecting those Office 365 credentials is absolutely critical.
What can be done to protect this information? Microsoft has a solution called Advanced Threat Protection, which checks attachments as well as links to make sure they are okay before a user can click on them. In the case of the above email, if a user clicked on the “Validate-Here” link they would see the following:
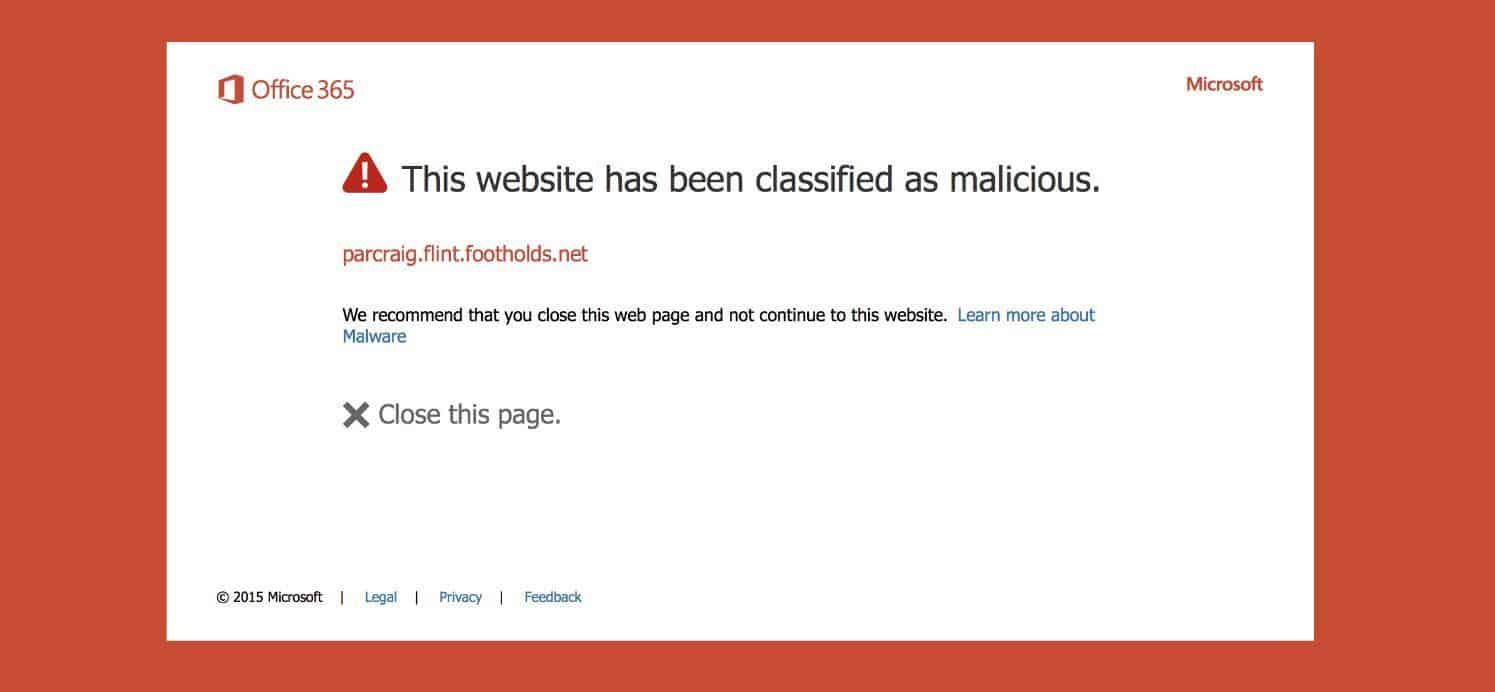
But technology is not enough, as almost all protection technologies are reactive in nature – something bad has to happen before these systems can learn and stop the attacks. The key is end user education. We need to continually train our end users on what is “normal” and what should trigger them to be suspicious. End users are our last line of defense, and we need to arm them with the information so the next time they see an email like the one above, they ASK before opening it. Once we get that tendency to question things strongly ingrained in our users, we can start to win the battle…
If you have questions about getting your team up to speed on security best practices and teaching them how to recognize threats, our Security Awareness Training can help. Feel free to reach out to us with any questions about security or 0365, our experts are happy to help.
